Not so long ago I was researching the different ways to secure a web application from hackers and other bad guys. Accidentally I stumbled upon a new technology in this field called RASP. The RASP stands for Runtime application self-protection. The technology looks quite promising and concentrated on the protection of an application from the inside. This aspect of RASP is quite opposite to other well-known approaches to the application security, e.g WAF or IDS/IPS. Let’s quickly revise the basic info about these approaches.
IPS/IDS
The IPS/IDS is the oldest technology among mentioned, and it has already proved to be useful. The main idea of the IPS/IDS is that they sit on the network, between your app and the client and monitor the network traffic for the sights of malicious data. The other useful function of such systems is a DDoS attacks prevention. IPS/IDS can be present both: hardware and software forms.
The main drawbacks of such systems:
- They struggle to work with encrypted traffic (e.g. HTTPS);
- They mostly perform the simplest checks and perform no behavioural analysis and thus would not help with e.g bot detection;
- They are mostly written in C/C++ and have middle-to-big codebases, so they are hard to extend.
Well-known software systems of such a type are:
WAF
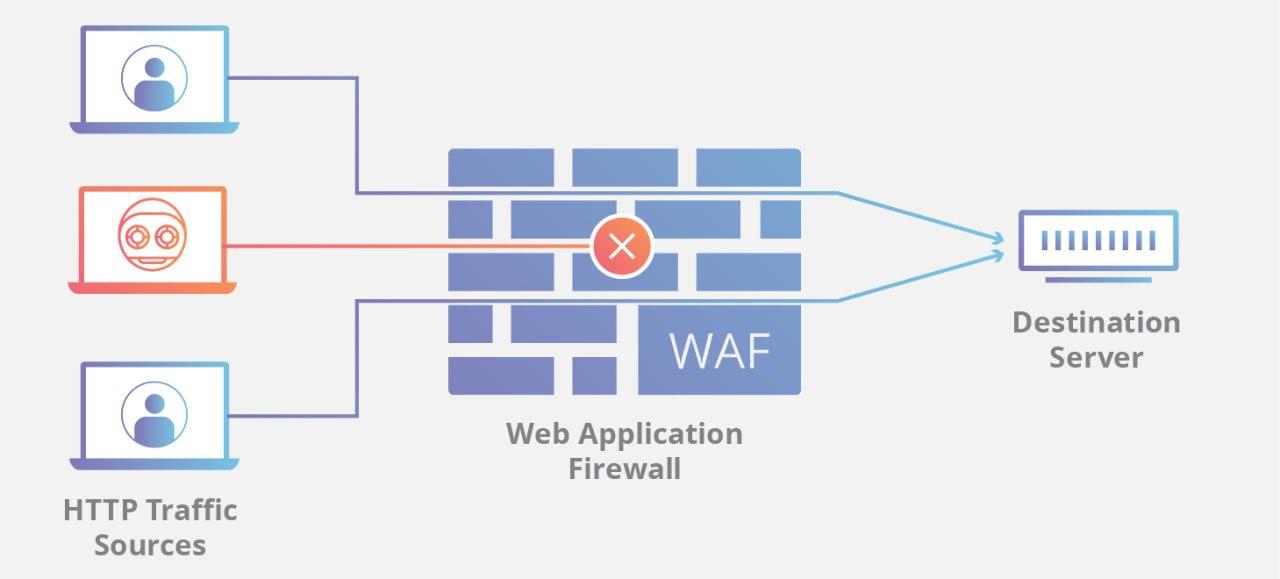
The WAF stands for Web application firewall, and it is usually just OSI Level 7 application which addresses the IPS/IDS issues with HTTPS and extensibility. Usually, WAF can provide the same functionality as an IPS/IDS system, however it will have a poorer performance characteristics and support a lot less protocols that Enterprise level IPS/IDS.
The WAF basic functionality includes:
- IP blacklisting/whitelisting;
- OWASP Top 10 attack prevention (e.g. prevention of the SQL injection or XSS attack based on some content-scanning rules);
- Behavioral analysis (rare feature).
The WAF is a good fit to cover the holes left by the IPS/IDS, however you would still pay the cost of the one more agent between a client, and your web app (network round-trip cost, content analysis cost and so on). There a lot of open-source WAF out there. The AWS WAF may serve as an example of an WAF as a Service.
RASP
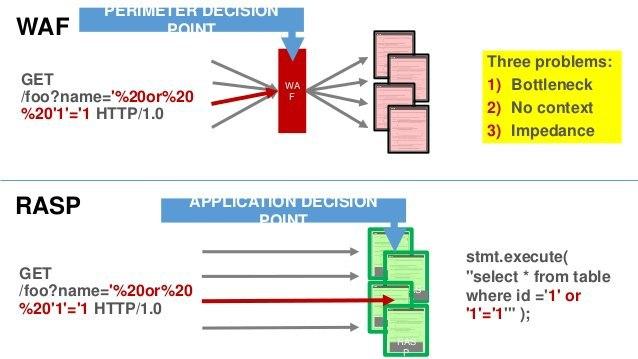
Here RASP comes to the rescue. The main idea of RASP is that all the application protection logic is directly integrated into your program. In such a way RASP eliminates at least part of the WAF performance impact and, also get access to your app intrinsics which can help with vulnerable code-path determination and access prevention for only specific clients/actions.
Currently, open-source RASP solutions exist only for Java and PHP (at least I have found only this one). With Java, for example, to integrate the RASP into application the java agents and thus code instrumentation is used.
The code instrumentation in Java basically allows the java agent to intercept any method calls and object interactions and gives RASP agent the ability to monitor and block any actions that happen in the code.
Nowadays RASP solutions can deal with XSS, CSRF, SQL injection and other well-known attacks, however the field is quite new, so there is no strong guaranties that RASP will block all the well-known attacks.
The main drawback of RASP from Java perspective is an agent usage. A lot of enterprise application already use some agents for things other than security and when you add many agents to your application things can get messy, agents can conflict and crash the JVM.
If you want to find out a bit more about the RASP technology I would recommend reading this paper and looking into the code of the OpenRASP